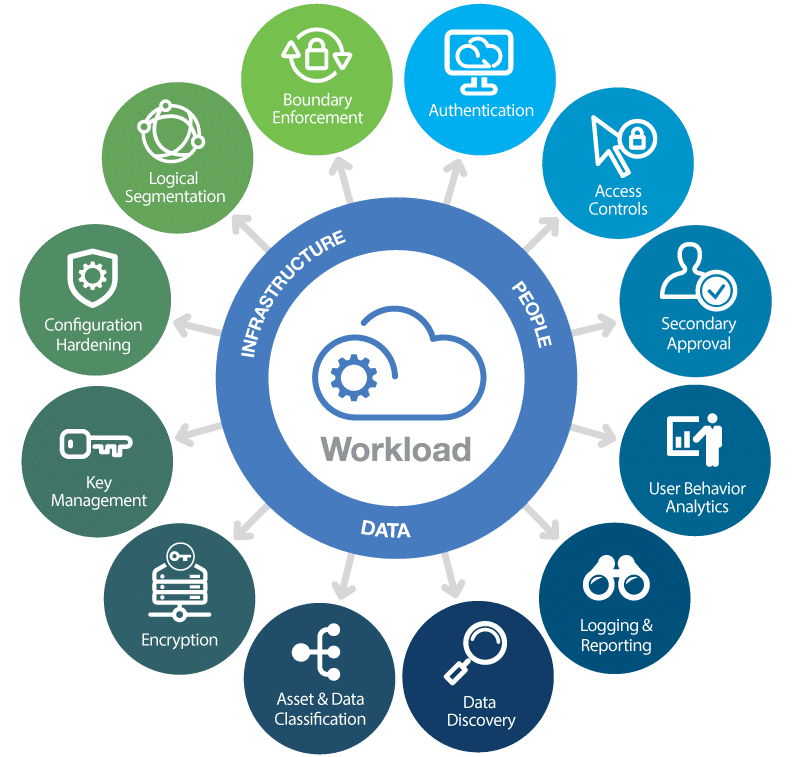
Cloud security is a paramount concern in today’s digital landscape, as businesses increasingly rely on cloud environments for their data storage needs. With the rise of cloud data protection solutions, organizations aim to mitigate the risks associated with cloud storage, including potential data breaches and loss of sensitive information. Despite the challenges posed by cloud storage risks, such as inadequate security measures and compliance issues, it remains essential for companies to implement effective data breach prevention strategies. Investing in robust cloud provider security is crucial for maintaining customer trust and ensuring organizational stability. By prioritizing cloud service compliance, businesses can protect their assets while reaping the benefits of flexible and efficient cloud solutions.
Digital asset protection in the cloud has become an essential focus for businesses navigating through the complexities of modern technology. Known by various terms such as cloud-based security infrastructure or online data safeguarding, it encompasses measures to ensure data integrity and confidentiality in remote storage solutions. The evolving landscape of digital information requires a deep understanding of potential vulnerabilities to mitigate issues related to third-party access and data misuse. Organizations must adopt comprehensive strategies that encompass both proactive security measures and regulatory compliance requirements. As they transition to online storage systems, prioritizing effective safeguards is imperative to secure their sensitive information against emerging threats.
Understanding Cloud Security: Why It Matters
Cloud security is an essential element for any business leveraging cloud storage solutions. It refers to the set of policies, controls, and technologies that work together to protect cloud data, applications, and infrastructure from threats. With the increasing reliance on cloud services, businesses must prioritize robust cloud security measures. This includes understanding how to protect cloud data from vulnerabilities due to cyberattacks, data breaches, and compliance violations. As cyber threats continue to evolve, a strong emphasis on cloud security can help create a safer digital environment for critical business information.
The timeline of recent data breaches has highlighted the challenges many organizations face in maintaining cloud security. The alarming statistics show that a significant number of businesses lack adequate security measures, leading to increased risks of data breaches. Investing in cloud security thus not only prevents potential financial losses but also nurtures consumer trust. Companies providing cloud services tend to prioritize security due to the potential impact of data breaches on their reputation and financial standing, making them generally more secure than individual businesses attempting to manage their own data on-site.
Cloud Data Protection Strategies
Implementing effective cloud data protection strategies is crucial for businesses seeking to safeguard their information. This involves utilizing various methods and technologies to secure sensitive data stored in the cloud. Techniques such as encryption, multi-factor authentication, and regular backups play a vital role in ensuring the safety and integrity of cloud data. Furthermore, developing a data classification policy helps businesses understand their data types and establish appropriate security measures tailored to sensitive information.
Moreover, businesses should regularly assess and update their data protection strategies to adapt to emerging threats and compliance requirements. Regular evaluations help identify potential vulnerabilities in the system and offer opportunities to fortify defenses against data breaches. By leveraging advanced cloud data protection features offered by reputable providers, such as robust encryption methods and comprehensive backup solutions, organizations can build a resilient framework that protects against unauthorized access and potential data loss.
Navigating Cloud Storage Risks
While cloud storage offers numerous advantages, it’s essential for businesses to navigate the inherent risks associated with this technology. One significant risk involves data breaches, where sensitive information becomes accessible to unauthorized entities. Understanding the specific risks related to cloud storage helps enterprises take appropriate measures to mitigate them, such as selecting a compliant cloud service provider that prioritizes security. Additionally, putting in place regular audits and utilizing security tools can help businesses recognize and address vulnerabilities before they are exploited.
Another concern with cloud storage is the potential for compliance issues. Organizations need to ensure that the cloud provider adheres to regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Failure to comply can lead to significant penalties and legal repercussions. By working closely with cloud providers and continuously monitoring compliance standards, businesses can effectively manage these risks and maintain secure cloud storage practices.
Essential Data Breach Prevention Techniques
Data breach prevention should be a primary concern for any organization using cloud services. Implementing a comprehensive security framework is one of the most effective ways to protect sensitive data from malicious attacks. This includes using strong authentication methods, such as two-factor authentication, to ensure that only authorized users can access sensitive information. Regularly updating software and implementing effective intrusion detection systems can help identify potential threats before they result in significant breaches.
Education and training for employees also play a crucial role in preventing data breaches. Workers should be trained on best practices regarding data security, including recognizing phishing attacks and ensuring secure information sharing procedures. Ultimately, cultivating a company-wide culture of security awareness acts as an additional layer of protection, significantly lowering the risk of data breaches caused by insider threats or human error.
The Importance of Cloud Service Compliance
Compliance with industry standards and regulations is imperative for cloud service providers. Organizations must determine whether potential cloud providers comply with essential regulations, such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR). Non-compliance can expose businesses to legal liabilities and financial penalties, further eroding trust with consumers and clients. Engaging with compliant cloud service providers shields businesses from risks associated with data violations.
Additionally, regular compliance audits provide organizations with insights into possible areas of improvement. These audits examine whether cloud providers maintain robust security protocols, accurate documentation, and adherence to established regulations. By prioritizing working with compliant providers, businesses can mitigate the risks posed by potential data breaches and enhance the overall security of their cloud environments.
Choosing the Right Cloud Provider for Enhanced Security
Selecting the appropriate cloud provider is crucial for enhancing data security across all business operations. Potential customers should evaluate prospective providers based on their security measures, compliance level, and the technologies they can implement to safeguard data. For example, a reputable cloud provider should offer essential features such as encryption, secure access controls, and regular security updates to mitigate vulnerabilities.
It is also beneficial to inquire about the physical security measures in place. Experts recommend looking for providers with advanced security protocols, such as 24/7 human monitoring, biometric access controls, and video surveillance. Such measures act as deterrents against physical breaches, ensuring the data stored in the cloud remains safe from unauthorized access.
Utilizing Encryption for Enhanced Cloud Security
Encryption serves as one of the most effective tools for securing cloud data. By converting sensitive information into coded language, encryption prevents unauthorized access, ensuring that only individuals with the correct decryption keys can read the data. Businesses that prioritize encryption when storing data in the cloud significantly reduce their vulnerability to data breaches, ultimately protecting client information and sensitive business records.
Furthermore, businesses should consider encrypting data both at rest and in transit to enhance security across all stages of storage. Implementing robust encryption protocols helps create a multi-layered security approach, making it more challenging for hackers to exploit vulnerabilities. Companies that leverage industry-standard encryption technologies demonstrate to their stakeholders a commitment to data protection and responsible cloud computing practices.
The Role of Physical Security in Cloud Services
While many focus on digital security measures, physical security remains a crucial aspect of cloud services that should not be overlooked. Cloud providers must invest in robust physical security measures to safeguard the data centers where customer data is stored. Effective physical security includes access control systems, surveillance cameras, and security personnel to prevent unauthorized entry into sensitive environments.
In addition, ensuring that these data centers have appropriate environmental controls in place—like temperature regulation, fire suppression systems, and uninterruptible power supplies—further fortifies overall security. Cloud service customers should prioritize potential providers that can demonstrate their commitment to physical security, as this adds an additional layer of protection against data breaches and operational disruptions.
Building a Resilient Disaster Recovery Plan in the Cloud
A resilient disaster recovery plan is essential for organizations that operate in a cloud environment. Despite the higher security measures and controls offered by cloud providers, data loss still remains a risk due to unforeseen natural disasters, cyberattacks, or server failures. Businesses should ensure they have proper data backup mechanisms and recovery options in place to restore access quickly during incidents, minimizing downtime and potential financial losses.
Additionally, companies must regularly test their disaster recovery plans to ensure they can effectively respond to emergencies. These simulations help identify weaknesses within the recovery process and allow organizations to refine their strategies. By selecting a cloud provider that offers robust disaster recovery solutions, businesses can establish a strong framework, ensuring data remains secure and recoverable when faced with unexpected challenges.
Frequently Asked Questions
What is Cloud Security and why is it important for businesses?
Cloud security refers to the measures and technologies that protect cloud computing environments, including data storage, applications, and infrastructure. It is crucial for businesses because it safeguards sensitive information from breaches, ensures compliance with industry regulations, and protects against data loss during cyberattacks or natural disasters. Given the increasing incidents of data breaches, investing in cloud security helps maintain trust and reliability in cloud services.
How can businesses ensure Cloud Data Protection when using cloud services?
To ensure cloud data protection, businesses should choose reputable cloud providers that implement advanced security measures such as encryption, identity and access management, and regular security audits. Additionally, employing multi-factor authentication and ensuring that data is backed up across multiple locations can further enhance data protection in the cloud. Regular training on security best practices for employees is also vital.
What are the common Cloud Storage Risks businesses should be aware of?
Common cloud storage risks include data breaches, unauthorized access, data loss, compliance violations, and inadequate physical security. Businesses can mitigate these risks by understanding the security measures offered by their cloud service provider and implementing their own security protocols such as encryption, monitoring, and access controls.
How does Data Breach Prevention work in cloud environments?
Data breach prevention in cloud environments involves several layers of security, including encryption of data at rest and in transit, robust authentication processes, and continuous monitoring for unusual activity. Additionally, implementing strict access controls and regularly updating security policies help protect against potential breaches. Continuous audit trails can also provide insights to identify vulnerabilities before they are exploited.
What aspects of Cloud Service Compliance should businesses consider?
Businesses should consider whether their cloud provider adheres to relevant industry regulations and standards, such as PCI DSS, HIPAA, or GDPR. It is essential to verify that the provider undergoes regular compliance audits and can demonstrate their security measures through certifications. By ensuring cloud service compliance, businesses protect their data integrity and reduce legal liabilities.
Why is cloud provider security crucial for protecting company data?
Cloud provider security is crucial because providers often have greater resources to implement advanced security solutions compared to individual businesses. They invest in cutting-edge technologies, skilled personnel, and compliant infrastructure to protect customer data. By entrusting data to a secure cloud provider, companies can benefit from these heightened security measures while focusing on their core operations.
What questions should businesses ask to evaluate potential cloud providers’ security?
When evaluating potential cloud providers, businesses should ask about their data encryption practices, physical security measures for data centers, compliance with industry standards, backup practices, and methods for data restoration. Questions about how they handle cyber threats and their response plans can also provide insights into their security preparedness.
How can companies prepare for a potential data breach in the cloud?
Companies can prepare for potential data breaches in the cloud by creating an incident response plan that outlines steps to take in the event of a breach. Regularly updating security protocols, conducting penetration testing, and training staff on recognizing suspicious activities are essential components of a proactive security strategy. Additionally, maintaining regular backups ensures data can be restored quickly if compromised.
What is the role of encryption in Cloud Security and Data Protection?
Encryption plays a critical role in cloud security and data protection by converting sensitive information into a coded format that can only be accessed with the correct decryption key. This ensures that even if an unauthorized party gains access to the data, they cannot read it. Implementing strong encryption protocols enhances the overall security posture of cloud storage solutions.
What measures can be taken for secure Cloud Storage to protect business data?
To secure cloud storage, businesses should choose providers that offer features like end-to-end encryption, regular security updates, and strong access controls. Additionally, utilizing private networks, multi-factor authentication, and routine security assessments can further safeguard business data stored in the cloud. Regular training for employees on security practices is equally important.
| Key Point | Explanation |
|---|---|
| Impact of Hacks | Recent media reports highlight that while consumer services are often targeted, businesses should also be concerned for their data security. |
| Risk of Cloud Storage | Despite security concerns, dedicated cloud storage often provides better security than local backups, which may be more vulnerable. |
| Compliance Issues | A significant number of businesses that were hacked were not compliant with essential security standards like PCI DSS. |
| Cloud Provider Security | Reputable cloud providers typically invest heavily in security and physical safety measures, making them less appealing targets for hackers. |
| Choosing the Right Provider | Businesses must vet cloud providers carefully, asking questions about their security practices and backup processes before migrating. |
| Isolation & Compartmentalization | Providers should implement robust methods to ensure that data from different clients is kept secure and isolated from each other. |
| Encryption and Access Control | Effective cloud solutions include strong encryption for data transfers and strict access regulations to protect sensitive information. |
Summary
Cloud security continues to be a vital concern for businesses as they navigate the complexities of data management in today’s technological landscape. The rise in cyberattacks and data breaches has heightened awareness surrounding the safety of off-site data, particularly in shared cloud environments. Businesses that are cautious about moving to the cloud must recognize that reputable cloud providers often offer enhanced security measures compared to traditional local backups. By thoroughly vetting potential providers and ensuring they adhere to stringent security protocols, businesses not only protect their valuable data but also build a safer digital future.